Cybercrimes Right Under Your Noses: What You Don't Know Cybercriminals Might Be Doing to You5/11/2020
The numbers are growing and it is alarming that it does not only involve big names in the different industries. Cyberattacks excuse no one and do not make anyone immune. Attacks do not only involve the company’s system and hackers alone. Sometimes, it involves your employees or even yourself unknowingly. This is the reason why you must be able to identify possible attacks and be cautious enough for any malicious activity. It can happen any time so you need to have enough knowledge about the types of cybercrimes that you might encounter. Types of Cybercrimes Cybercriminals Might Be Doing To You Phishing One of the common and widespread attacks for many businesses over the years, phishing is a type of attack that generates a fake email, website, or even text message that contains a malicious link. It tricks its recipient to click on the link associated in the email or messages and once clicked, it can create access to infiltrate the company’s system or be able to farm our sensitive information like password combination, credit card info, personal information, login credential and other information that is of value to them. The messages used in phishing attacks can range from any random topic that makes it difficult to detect by most recipients. Attacks are often used names of companies that you may trust or a real or plausibly real entity that you have worked with. How does it work?
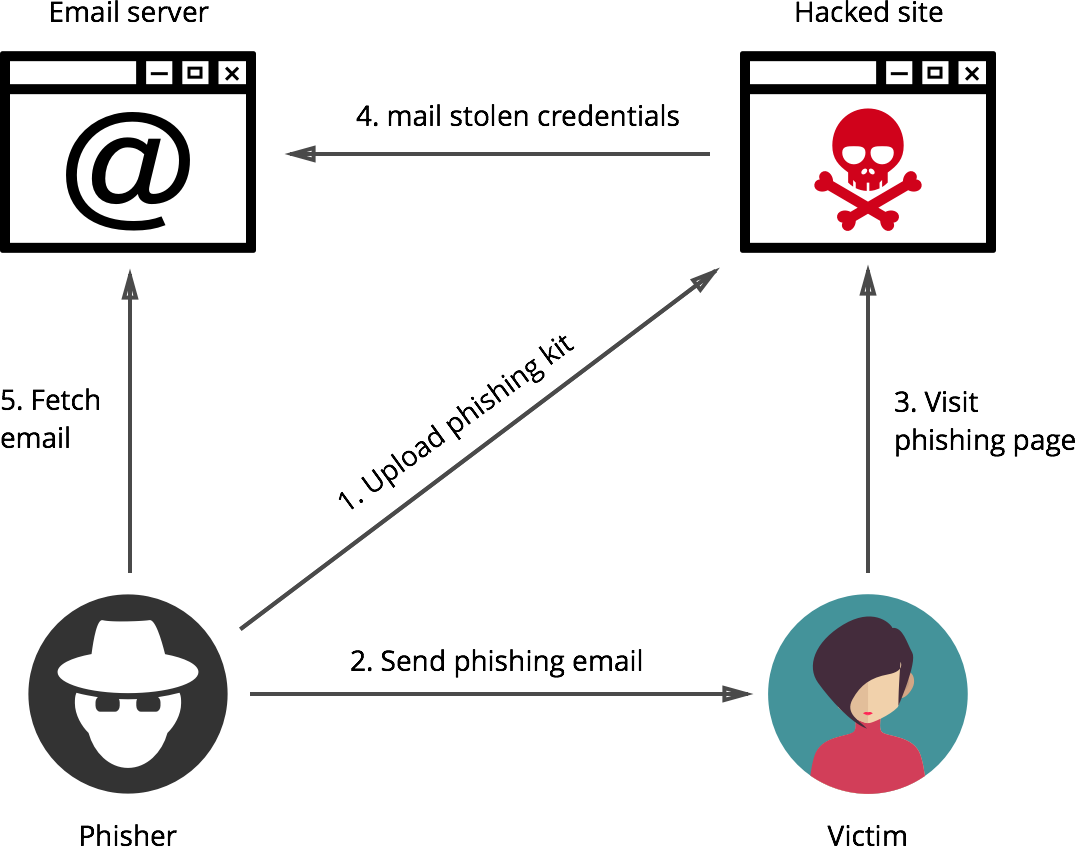
Cybercriminals and attackers first identify which business they will target and plan out how to get the email addresses of customers associated with the company. Once proven that the identified company’s site is vulnerable, a phishing kit is then uploaded to the website. The attackers then send a spoofed message usually in an email format containing a phony message that appears to be from a reliable source. Once the receiver or victim visits the phishing page and uses his login credentials, it will be then mined by a PHP script which will send it to an email controlled by the attackers. From then on, cybercriminals will now use these credentials to do any ill-mannered activities.
DoS and DDoS Denial of Service (DoS) is a type of attack that can make your system stop working or even take down your website to make it unavailable. It can either send specialized data that can cause an error in your system to make it stop working or overload your system or overwhelm your website with traffic to disrupt its activity causing it to crash down. A DDoS or distributed Denial of Service happens when the attack is carried out to a multiple set of computers. How does it work? There are several ways to conduct a DoS or DDoS attack: Buffer Overflow The most common kind of DOS attack. The concept of this attack is to send additional traffic to a network of addresses than the specific number of visitors programmers built in the system to handle. ICMP This is done by sending spoofed packets to every computer on a targeted network. The spoofed packet would then ping all of the computers, then trigger the network to amplify the traffic. SYN flood Targets all open ports with requests to connect to a server. Once all the ports are saturated with requests, there will be no available for legitimate users to connect to. Others forms Takes advantages of bugs that can crash or severely destabilize the system. Malware A term that means malicious software, these are programs that are embedded into your computer without your knowledge and right under your nose. Malware can cause serious damage or a massive data breach. How does it work? Since different kinds of malware can affect a system, here how the common types of work: Ransomware – The most expensive type of malware you can encounter. It can lock an entire system or steal computer files that you can regain access by paying a sum of money. However, paying is not usually the solution since some hackers still deny access even though ransom money has been paid amplifying the cost more. It is usually delivered via email that entices an employee or a recipient to click a click or download an attachment containing the malicious software. Virus – Infect clean files by attaching themselves to it. It spreads easily and uncontrollably which results in deleting and corrupting files. Trojans – often disguised as software or hidden in software, it can act discreetly and then create a backdoor in your security that can be accessible to other malware. Worms – This type of malware can infect a network of devices. As it uses network interface, it can infect local computers or across the internet and con. IoT-Based Attacks Technology has given us the ability to connect people and things even with a physical distance challenge. One of the trends that have been emerging is the Internet of Things or the ability to connect “smart” devices in homes and businesses. These have revolutionized how technology has been adopted to homes but also has given new threats for cybersecurity. How it works: The problem however is not all smart devices interconnected are protected properly having a weak cybersecurity system installed. This poses a great risk as this creates an opening where cybercriminals can hijack these devices to disrupt the connection and eventually create attacks. Insider Threat and Attack Having a strong security system sometimes is not enough. Especially if the attacks happened because of someone in the organization or one of the internal users of the system unintentionally and maybe intentionally at some point became the source of why the attack happened. This could be the biggest cybersecurity threat that you have under your nose. Oftentimes, these attacks are caused by mistakes and negligence. How it works: When employees do not have any regular and hands-on security awareness seminars and training, they will not be able to distinguish even a malicious email. They may also happen if you do not update cybersecurity in your company and do enforce any security protocols. When employees are knowledgeable when it comes to possible cyber-attacks, they can be your greatest asset in protecting your company. Final Thoughts A lot of businesses succumb to cyberattacks because of not taking cybercrimes seriously. Many only address their cyber vulnerabilities when they experience being threatened. As a business owner, you must protect your hard-earned investments. You need to improve your cybersecurity and be wary enough that the next attack may target you. It is important to note also that no matter how strong your security system is, there would be no better option to protect your company from any security threats by educating your employees and yourself as well. Employees at all levels are at risk of any vulnerabilities that can lead to an attack. Many big companies suffered from big attacks because of a single employee mistake. It is also essential that you and your staff are malicious enough or curious enough to check any dubious emails. Always update your system It will not hurt to verify so you will prevent any attack happening under your nose and without you knowing.
|
Categories
All
Archives
November 2023
|
|
Locations:
New Orleans, LA Nashville, TN |
|
Digital Media Ghost @2020
|



 RSS Feed
RSS Feed
